In the digital age, “Mr Robot” has popularized hacking, transforming it from a niche skill into a mainstream phenomenon. While media often glamorizes the thrill of hacking, it’s crucial to understand the real-world implications and techniques behind it. This blog delves into five tech hacks that can make you feel like a character from Mr. Robot, exploring tools and tactics used by both ethical hackers and malicious actors. From phishing and Wi-Fi password cracking to dark web navigation and Bad USBs, we provide a comprehensive guide to these fascinating yet formidable techniques. Whether you’re an aspiring ethical hacker or simply curious, read on to equip yourself with knowledge that combines excitement with caution.
Table of Contents
1. Phishing Attacks and Social Engineering

What Are Phishing and Social Engineering Attacks?
Phishing attacks and social engineering are some of the most common techniques used by hackers to gain access to sensitive information. These attacks can be carried out through various means, such as email, instant messaging, or phone calls, and often involve tricking the victim into divulging their login credentials or other sensitive information.
Despite being one of the simplest phishing and social engineering attacks, it is simple and easy to execute. It also has a very high impact. There has been evidence in the past that more than 90 percent of cyber attacks come from these, and there are big examples.
Recent Attacks
- Google Docs Phishing (2017): A widespread phishing campaign where users received fake Google Docs links leading to a phishing page.
- Spear Phishing Targeting Sony Pictures (2014): Attackers sent convincing emails to Sony employees, leading to significant data breaches.
- IRS Impersonation Scams: Cybercriminals send fraudulent emails pretending to be from the IRS, especially during tax season.
- PayPal Phishing Attacks: Emails impersonating PayPal, claiming issues with accounts to trick users into clicking malicious links.
- COVID-19 Vaccine Phishing Scams (2020-2021): Exploited the pandemic by sending phishing emails related to vaccines.
- Business Email Compromise (BEC): Attackers pose as company executives to trick employees into making unauthorized financial transactions.
- Social Media Phishing: Fake login pages for popular platforms like Facebook and Twitter to steal credentials.
- Smishing (Phishing via SMS): Fraudulent text messages containing malicious links.
- Vishing (Phishing via Phone Calls): Scammers impersonate trusted entities to obtain personal information over the phone.
Scene in MR Robot Demonstrating Phishing
How to Avoid Them
- Be suspicious of unsolicited requests: No legitimate company will ask for sensitive information via email or text.
- Verify links and attachments: Contact the company directly if unsure about the legitimacy of a message.
- Limit information shared on social media: Avoid providing details that can be used in targeted attacks.
- Keep software updated: Install updates to protect against vulnerabilities.
Imagine yourself as a victim of a phishing attack. Your personal information has been stolen and you are now at risk of identity theft and fraud. You are also worried about the emotional impact of the attack. How would you feel?
Would you want to put someone else through that?
Phishing attacks are not worth the risk. Don’t do it.
But If you want to know how to do for educational purpose only then check out my blog on how to create phishing website using Zphisher tool
2. Wifite Tool for Wi-Fi Password Cracking
What is Wifite?
Wifite is a tool that automates the process of capturing packets and cracking Wi-Fi passwords, making it a favorite among ethical hackers for testing network security.
Features of Wifite
- Automatically detects and captures WPA handshake packets.
- Supports a variety of attacks, including dictionary attacks and bruteforce attacks.
- Can crack WEP and WPA passwords.
Before Understanding about Wifite You must understand TCP Hnadshake.
Understanding the TCP Handshake
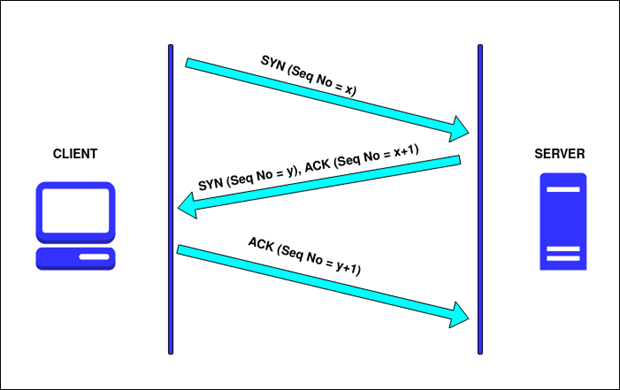
A TCP handshake is a fundamental process in network communication. By putting a Wi-Fi adapter into monitor mode, Wifite can capture these handshakes, which are essential for cracking WPA/WPA2 passwords.

Note that to perform this hack you must have your wifi adapter supporting monitor mode otherwise this attack wont be possible.
Bruteforcing the Handshake Capture File
- Handshake Capture Files: Contain Wi-Fi network authentication handshakes.
- Brute Force Attack: Attempts all possible password combinations.
You can use some of the famous automation tools for cracking passwords such as- Aircrack-ng: A popular Wi-Fi security tool.
- Hashcat: A versatile password cracking tool.
- John the Ripper: Known for its speed and efficience.
- Dictionary Attack: Uses a predefined list of words to guess the password.
- Popular Tools: Aircrack-ng, Hashcat, and John the Ripper.
Damage Potential
If an attacker gains access to your router, they can:
- Change settings: Disable security features or redirect traffic to malicious sites.
- Install malware: Exploit router vulnerabilities to infect devices.
- Monitor traffic: Steal personal information like passwords and credit card numbers.
- Launch DDoS attacks: Disrupt network availability or slow down performance.
Here is an Example from MR Robot demonstrating this hack
Checkout My article on WIFITE(Wireless hacking tool)
3. Bad USB Using Raspberry Pi Pico
What is a Bad USB?
A Bad USB is a malicious device that can steal data, install malware, or execute other harmful actions. It often masquerades as a legitimate USB device.
You will be shocked that it can be as cheap as $2/₹240 you can checkout here.
Making a Raspberry Pi Pico Bad USB
- Install CircuitPython: Follow instructions from the CircuitPython website.
- Modify code.py and payload.dd: Customize the scripts to perform specific actions when the device is connected.
- Upload files: Use the Thonny IDE to transfer files to the Raspberry Pi Pico.
Precautions and Damage
- Precautions:
- Inspect USB drives for tampering.
- Scan with antivirus software.
- Avoid using untrusted devices.
- Damage:
- Malware infection: Steal sensitive information.
- Data loss: Corrupt or damage files.
- System damage: Compromise operating system integrity.
Here is the demo of this attack used in MR ROBOT
4. Dark Web Exploration – Sneak Preview of How It Works
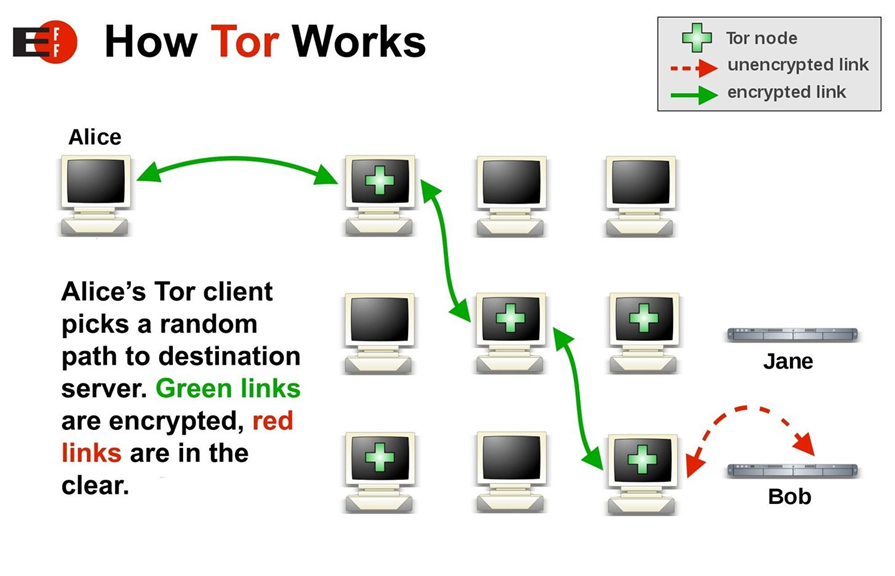
What is the Dark Web?
The dark web is a hidden part of the internet that is not indexed by traditional search engines. It can only be accessed through special software like the Tor browser. The dark web is notorious for its illegal activities such as drug trafficking, human trafficking, and cybercrime.
Benefits of Exploring the Dark Web
Despite its dangers, exploring the dark web can be beneficial for security researchers and law enforcement agencies to gather intelligence on cybercrime and other illegal activities.
The dark web is a hidden part of the internet, accessible only through specialized software like the Tor browser. It’s notorious for illegal activities but also used by researchers and law enforcement.
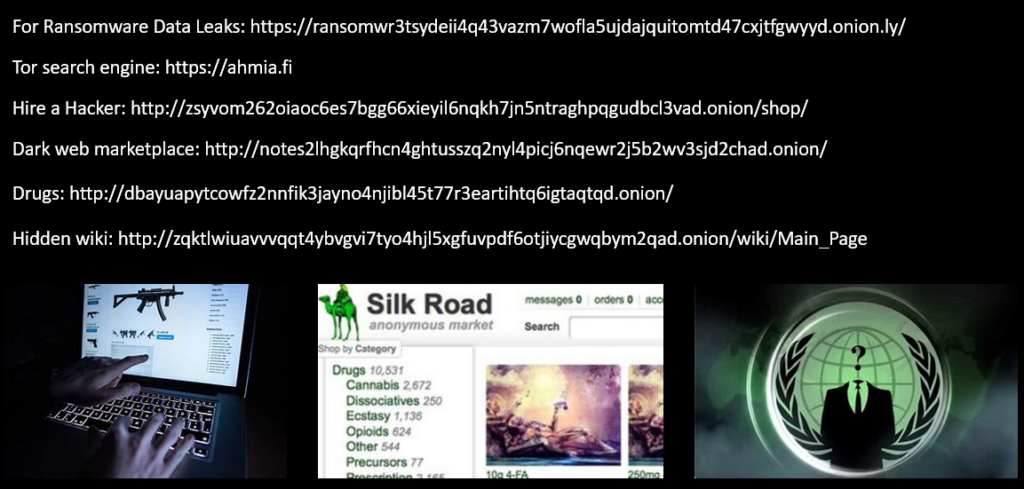
Benefits and Dangers
- Benefits:
- Gather intelligence on cybercrime.
- Research security vulnerabilities.
- Dangers:
- Exposure to scams and malware.
- Involvement in illegal activities.
How to Visit the Dark Web Anonymously

- Use Whonix: A secure OS that routes traffic through the Tor network, ensuring anonymity and protection from tracking.
- Caution: Only for educational purposes. Exercise extreme caution and legal compliance.
5. Other Cool Hacking Tools and Techniques Used in MR Robot
Ransomware
Ransomware is a type of malware that encrypts a victim’s files, demanding payment for decryption. It can cause significant financial and reputational damage.
Remote Access Trojan (RAT)

A RAT allows attackers to remotely control a victim’s computer. It can be used to steal information or launch further attacks.
Flipper Zero

A versatile device for interacting with digital systems. While useful for security research, it can also:
- Skim RFID tags: Steal contactless payment info.
- Clone NFC devices: Unauthorized access to secure areas.
- Control radio signals: Unlock cars or open garage doors.
- Deauthenticate Wi-Fi devices: Disrupt network access.
- Bad USB attacks: Infect computers with malware.
By understanding these techniques and tools, we can better protect ourselves and our networks. Remember, knowledge is power, but with great power comes great responsibility. Stay safe and ethical in your hacking endeavors.
Conclusion
In conclusion, understanding the tools and techniques used in hacking not only demystifies the processes but also highlights the importance of cybersecurity. From phishing attacks and Wi-Fi password cracking to the creation of Bad USBs and exploring the dark web, each method carries its own set of risks and ethical considerations. By familiarizing ourselves with these practices, we can better protect our personal information and networks from potential threats.
As you continue your journey into the world of cybersecurity, remember that knowledge is a double-edged sword. Use these insights responsibly and ethically to enhance security and foster a safer digital environment for everyone.
If you found this blog informative, be sure to check out my other posts for more insights into the fascinating world of ethical hacking and cybersecurity. Stay informed, by checking our blogs.

![You are currently viewing Top 5 Mr Robot Hacks [BUSTED]](https://gadgetsgeek.tech/wp-content/uploads/2024/06/wp1810658-mr-robot-wallpapers-scaled.jpg)